Your Cloud app security policies images are available. Cloud app security policies are a topic that is being searched for and liked by netizens now. You can Find and Download the Cloud app security policies files here. Find and Download all royalty-free photos.
If you’re looking for cloud app security policies pictures information connected with to the cloud app security policies keyword, you have pay a visit to the right blog. Our website always provides you with suggestions for viewing the maximum quality video and picture content, please kindly hunt and locate more enlightening video content and images that match your interests.
Cloud App Security Policies. After provision, you can also find the granted permission list from azure active directory admin center > enterprise applications > trend micro cloud app security > permissions. Custom cloud app security policies just wanted to start a conversation on what custom cas policies you find most useful. If necessary, you can integrate remediation workflows to achieve complete risk mitigation. Let’s break this down a bit.
 Microsoft Cloud app security notes from the field MS From msexperttalk.com
Microsoft Cloud app security notes from the field MS From msexperttalk.com
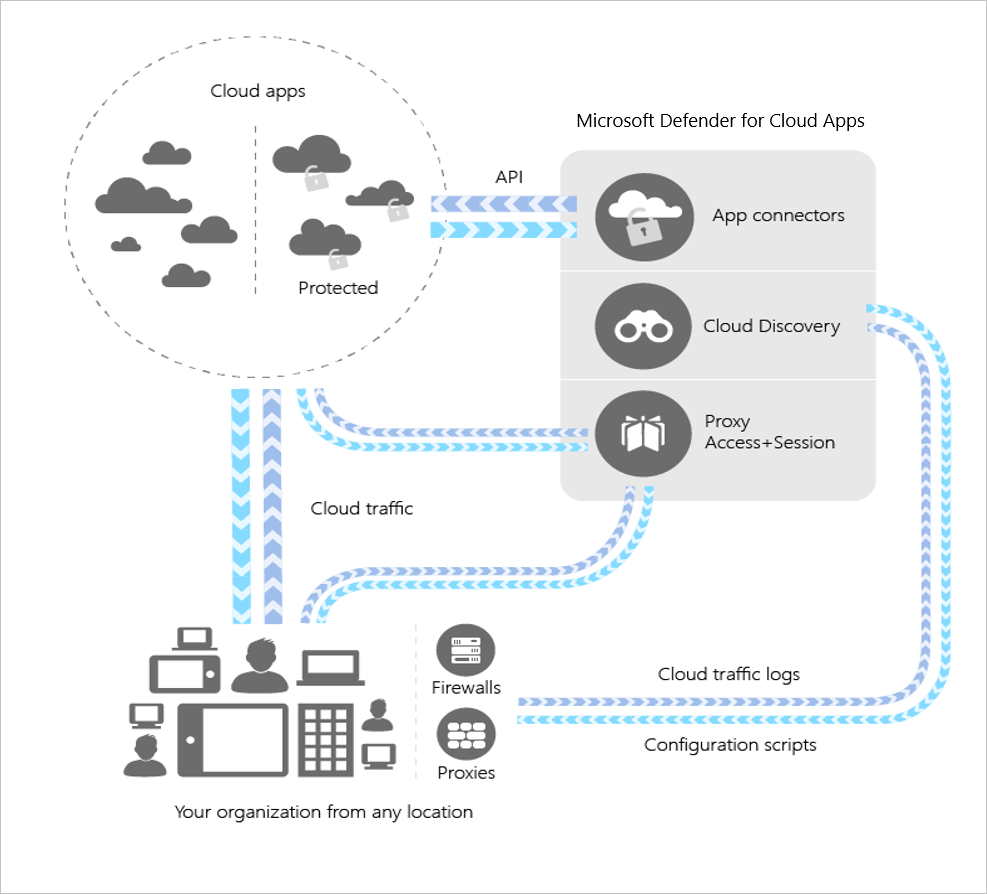
- create a new policy. In addition, microsoft defender for cloud apps now includes the capabilities of app governance and extends security features to more than 26,000 applications. Using cloud app security, we can create policies to, 1. From the choose saas list, select the cloud application for which to apply the new rule.; From the choose security list, select custom query. Access policies can be created for virtually any device, including those that aren’t even hybrid azure ad joined, nor managed by intune.
Only open ports when there�s a valid reason to, and make closed ports part of your cloud security policies by default.
Understanding casbs top 20 use cases for casbs (d). Bring in cloud app security. This policy applies to all targets in your company. During provisioning, microsoft authentication page will list the required permissions for you to review. From the choose security list, select custom query. To learn more about the recent renaming of microsoft security services, see the microsoft ignite security blog.
 Source: janbakker.tech
Source: janbakker.tech
After provision, you can also find the granted permission list from azure active directory admin center > enterprise applications > trend micro cloud app security > permissions. Let’s break this down a bit. Cloud app security provides two default atp policies for each protected application or service. To learn more about the recent renaming of microsoft security services, see the microsoft ignite security blog. Add a new policy rule button in the upper right area of the page.;

Understanding casbs top 20 use cases for casbs (d). In this example, i use office365 as the selected app, and windows 10 as the selected device platform, but you can adjust this to your own situation. Essentially, microsoft cloud app security works as a monitoring tool, a firewall, and an authenticator tool that protects your data and application at all times. From the choose security list, select custom query. Access policies can be created for virtually any device, including those that aren’t even hybrid azure ad joined, nor managed by intune.
 Source: youtube.com
Source: youtube.com
To create a custom query policy. There are plenty of activities to monitor, which ones have you considered worth while to monitor? Mcas is a monitoring tool that: This is a microsoft cloud app security (mcas) tech community space that provides an opportunity to connect and discuss the latest news, updates, and best practices with microsoft professionals and peers. For my first policy i will start by creating a new session policy from the policies screen.
 Source: docs.microsoft.com
Source: docs.microsoft.com
There are plenty of activities to monitor, which ones have you considered worth while to monitor? Cloud app security policies allow you to define the way you want your users to behave in the cloud. Since there isn�t a supported policy to monitor failed mfa results, aka, an adversary got the. The microsoft cloud app security product name has changed to microsoft defender for cloud apps. To clarify, integration with aip will leverage sensitivity labels if you have migrated your aip labels to.
 Source: docs.microsoft.com
Source: docs.microsoft.com
From the choose security list, select custom query. Provides visibility into the access of apps and data. For my first policy i will start by creating a new session policy from the policies screen. Cloud security policies are critical for organizations using the cloud to remain safe and compliant. From the choose security list, select custom query.
 Source: docs.microsoft.com
Source: docs.microsoft.com
This is a microsoft cloud app security (mcas) tech community space that provides an opportunity to connect and discuss the latest news, updates, and best practices with microsoft professionals and peers. First, we’ll need to route the application to cloud app security using conditional access. Click on the create policy drop down, then select access policy. Cloud services policy page 5 that deviate from the suit security program policies are required to submit a policy exemption form to suit for consideration and potential approval. If the cloud provider makes it available, use firewall software to restrict access to the infrastructure.
 Source: chrisonsecurity.net
Source: chrisonsecurity.net
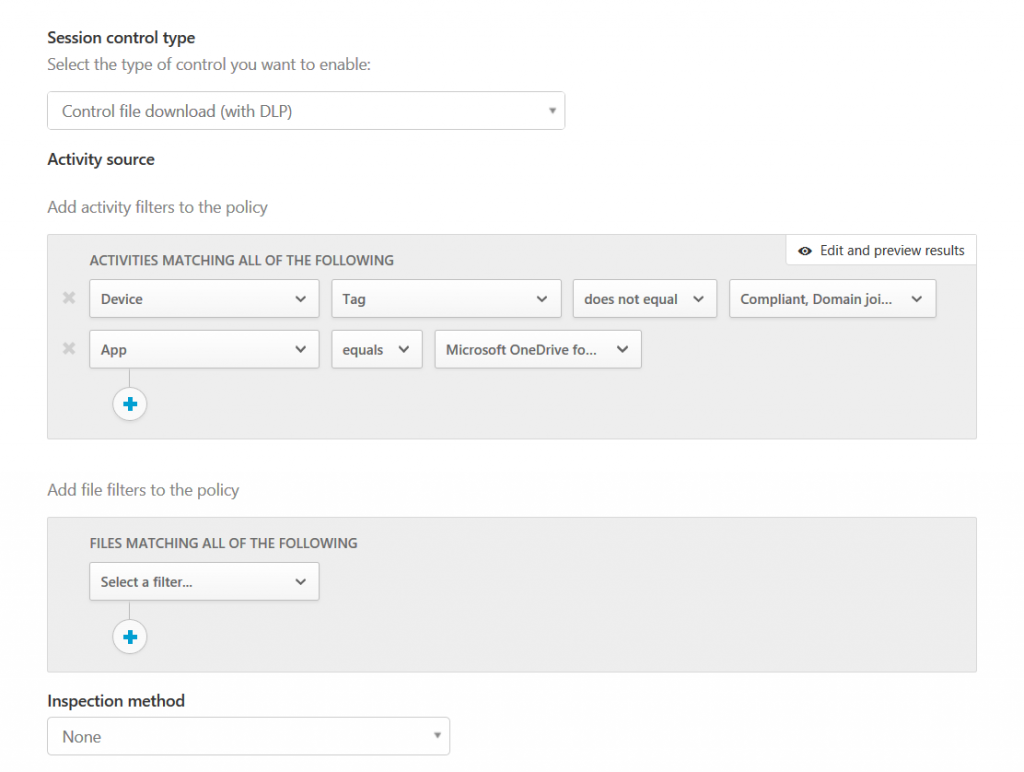
From the cloud apps security portal, expand control, and then policies. Understanding casbs top 20 use cases for casbs (d). If necessary, you can integrate remediation workflows to achieve complete risk mitigation. During provisioning, microsoft authentication page will list the required permissions for you to review. Custom cloud app security policies just wanted to start a conversation on what custom cas policies you find most useful.
 Source: youtube.com
Source: youtube.com
Bring in cloud app security. Add a new policy rule button in the upper right area of the page.; In addition, microsoft defender for cloud apps now includes the capabilities of app governance and extends security features to more than 26,000 applications. Essentially, microsoft cloud app security works as a monitoring tool, a firewall, and an authenticator tool that protects your data and application at all times. Understanding casbs top 20 use cases for casbs (d).
 Source: youtube.com
Source: youtube.com
Cloud security policies are critical for organizations using the cloud to remain safe and compliant. Configuring security policies, rules, and expressions. Let’s break this down a bit. If the cloud provider makes it available, use firewall software to restrict access to the infrastructure. 6 minutes this post walks thru an example of how to automatically apply a sensitivity label to files in sharepoint online and onedrive under certain conditions using an integration between microsoft cloud app security (mcas) and azure information protection (aip).
 Source: blog.mashfords.com
Source: blog.mashfords.com
Cloud security policies are critical for organizations using the cloud to remain safe and compliant. Access policies can be created for virtually any device, including those that aren’t even hybrid azure ad joined, nor managed by intune. You can create a custom policy that builds on existing policies of access, activity, file, oauth application, sessions or anomalies. Configuring security policies, rules, and expressions. They enable you to detect risky behavior, violations, or suspicious data points and activities in your cloud environment.
 Source: docs.microsoft.com
Source: docs.microsoft.com
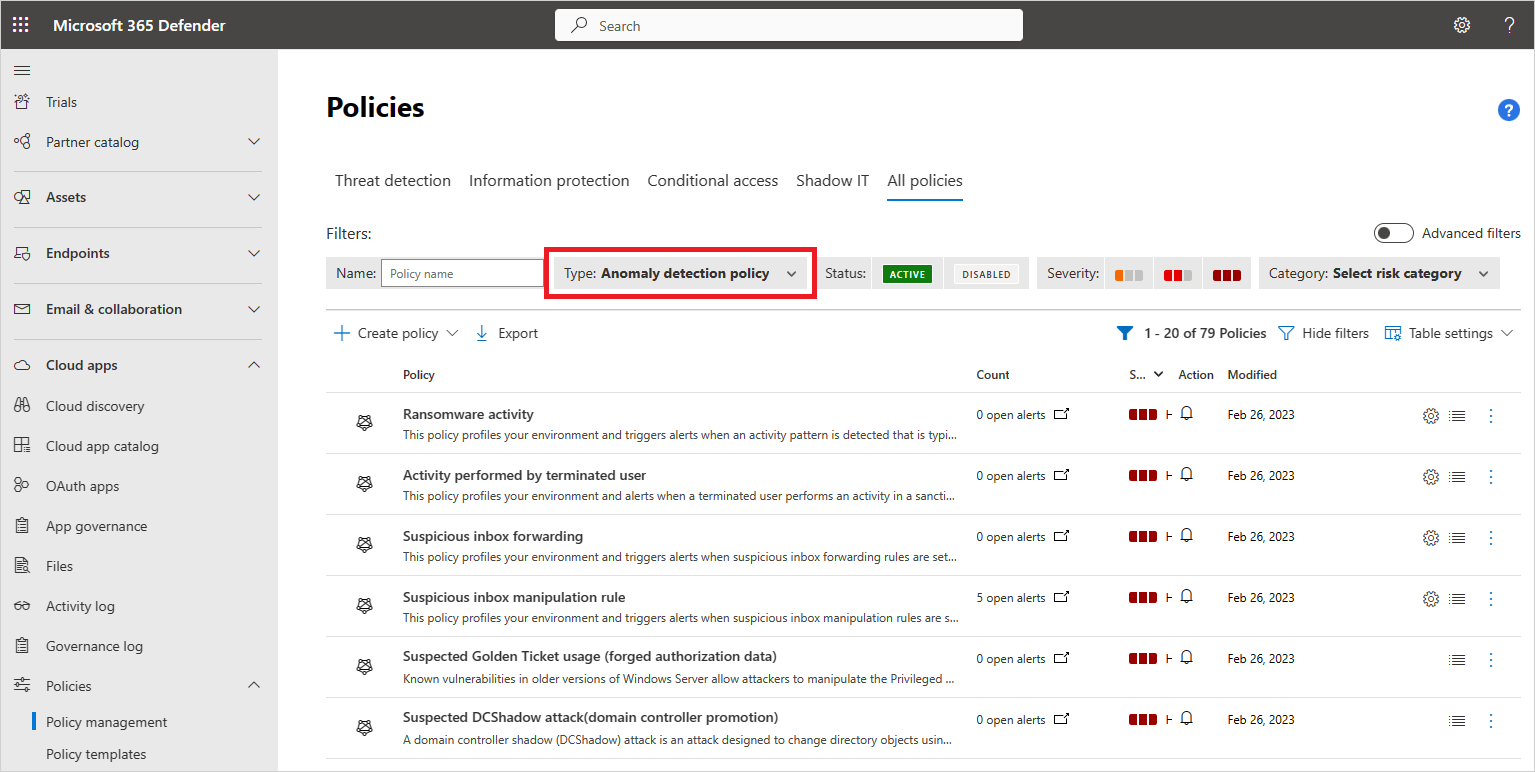
Click on the create policy drop down, then select access policy. Microsoft cloud app security (mcas) is included in enterprise mobility + security e5 and builds upon the mobility and security functionality that comes as part of e3, predominantly intune and conditional access. They enable you to detect risky behavior, violations, or suspicious data points and activities in your cloud environment. If necessary, you can integrate remediation workflows to achieve complete risk mitigation. From the cloud apps security portal, expand control, and then policies.
 Source: docs.microsoft.com
Source: docs.microsoft.com
To create a custom query policy. Plus sign (+) button next to the name of the cloud application.the new policy rule page displays. This policy contains preconfigured settings and you can change them as necessary. They enable you to detect risky behavior, violations, or suspicious data points and activities in your cloud environment. Blocking access to the cloud environment can be efficiently done with other methods, such as conditional access policies, and use cases for using mcas access policies are rare, but there are a few interesting ones.
 Source: israelclouds.com
Source: israelclouds.com
Cloud security policies are critical for organizations using the cloud to remain safe and compliant. Using cloud app security, we can create policies to, 1. If the cloud provider makes it available, use firewall software to restrict access to the infrastructure. From the cloud apps security portal, expand control, and then policies. Access policies can be created for virtually any device, including those that aren’t even hybrid azure ad joined, nor managed by intune.
 Source: docs.microsoft.com
Source: docs.microsoft.com
This policy applies to all targets in your company. Cloud services policy page 5 that deviate from the suit security program policies are required to submit a policy exemption form to suit for consideration and potential approval. Blocking access to the cloud environment can be efficiently done with other methods, such as conditional access policies, and use cases for using mcas access policies are rare, but there are a few interesting ones. Then, i create policy > session policy. Access policies can be created for virtually any device, including those that aren’t even hybrid azure ad joined, nor managed by intune.
 Source: docs.microsoft.com
Source: docs.microsoft.com
In addition, microsoft defender for cloud apps now includes the capabilities of app governance and extends security features to more than 26,000 applications. Plus sign (+) button next to the name of the cloud application.the new policy rule page displays. Since there isn�t a supported policy to monitor failed mfa results, aka, an adversary got the. Add a new policy rule button in the upper right area of the page.; This is a microsoft cloud app security (mcas) tech community space that provides an opportunity to connect and discuss the latest news, updates, and best practices with microsoft professionals and peers.
 Source: iboss.com
Source: iboss.com
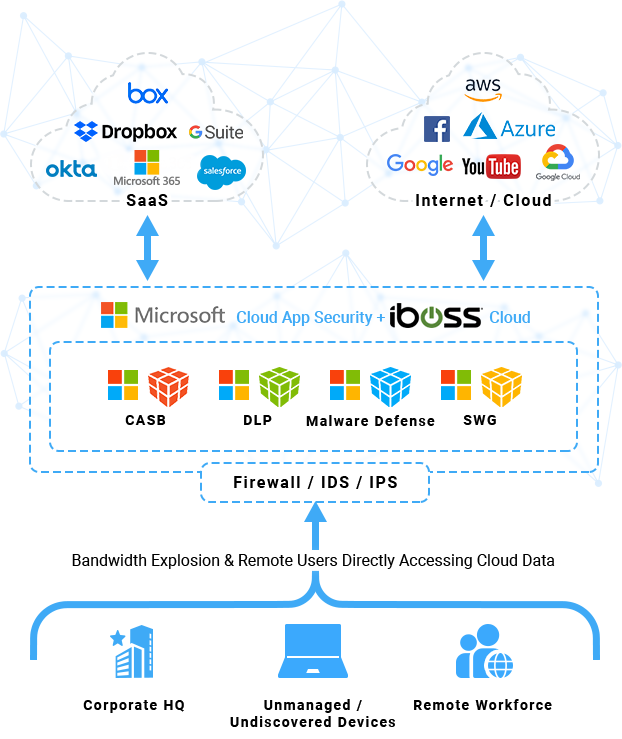
This is accomplished by pushing out. This is a microsoft cloud app security (mcas) tech community space that provides an opportunity to connect and discuss the latest news, updates, and best practices with microsoft professionals and peers. First, we’ll need to route the application to cloud app security using conditional access. To create a custom query policy. During provisioning, microsoft authentication page will list the required permissions for you to review.
 Source: docs.microsoft.com
Source: docs.microsoft.com
Since there isn�t a supported policy to monitor failed mfa results, aka, an adversary got the. In recent years, i have written +20 cloud app security (mcas) related blog posts but never touched deeply on access policies. Click on the create policy drop down, then select access policy. From the choose security list, select custom query. If the cloud provider makes it available, use firewall software to restrict access to the infrastructure.
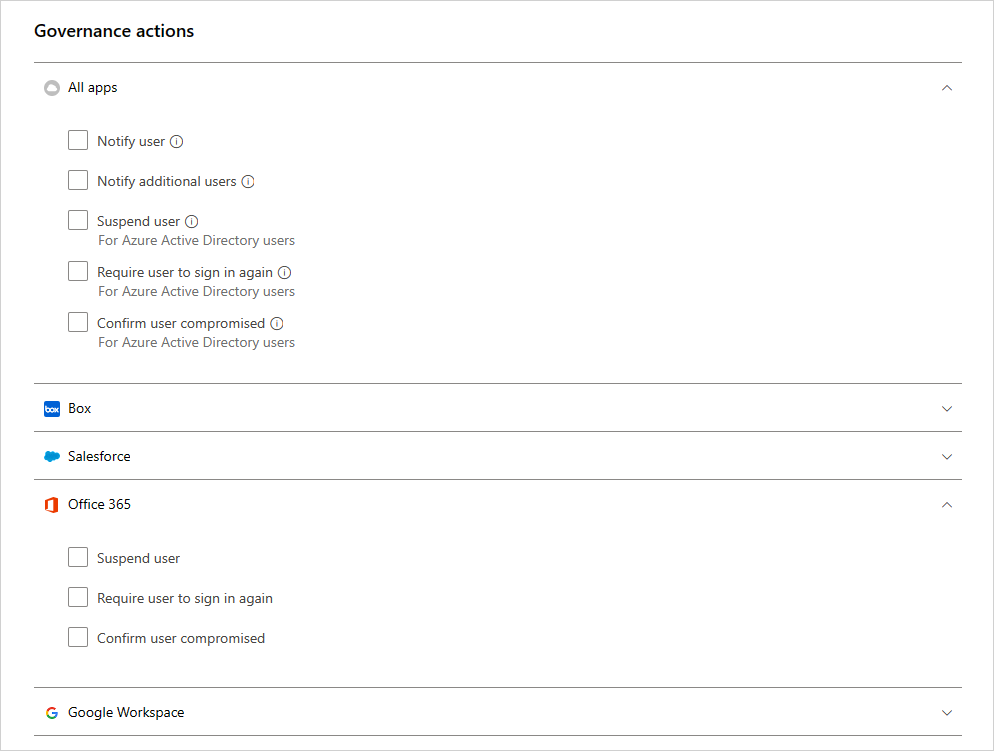 Source: docs.microsoft.com
Source: docs.microsoft.com
This policy contains preconfigured settings and you can change them as necessary. Cloud app security provides two default atp policies for each protected application or service. Let’s break this down a bit. This is a microsoft cloud app security (mcas) tech community space that provides an opportunity to connect and discuss the latest news, updates, and best practices with microsoft professionals and peers. Using cloud app security, we can create policies to, 1.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title cloud app security policies by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






