Your Cloud app security alerts images are ready. Cloud app security alerts are a topic that is being searched for and liked by netizens now. You can Download the Cloud app security alerts files here. Get all free photos and vectors.
If you’re searching for cloud app security alerts pictures information linked to the cloud app security alerts keyword, you have pay a visit to the ideal blog. Our site always provides you with hints for seeking the maximum quality video and image content, please kindly search and find more informative video articles and images that fit your interests.
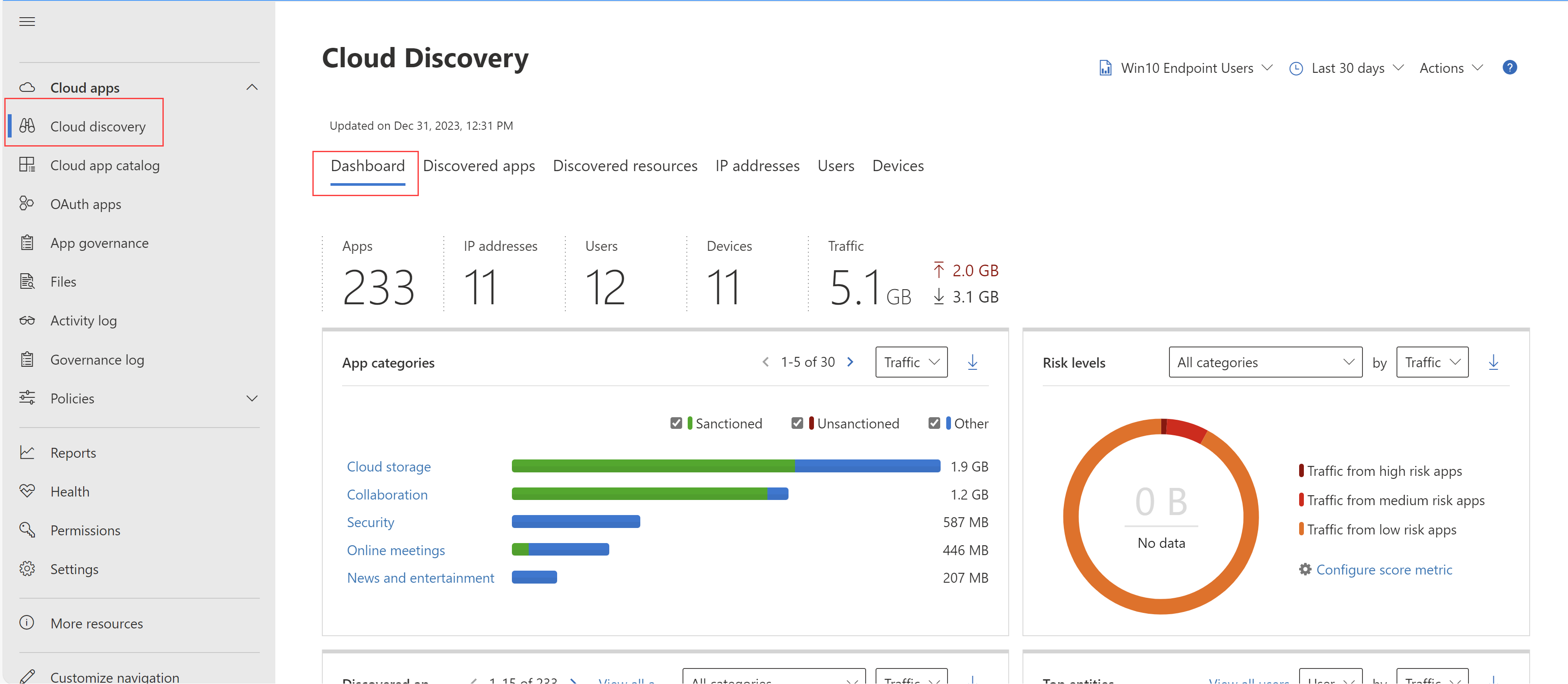
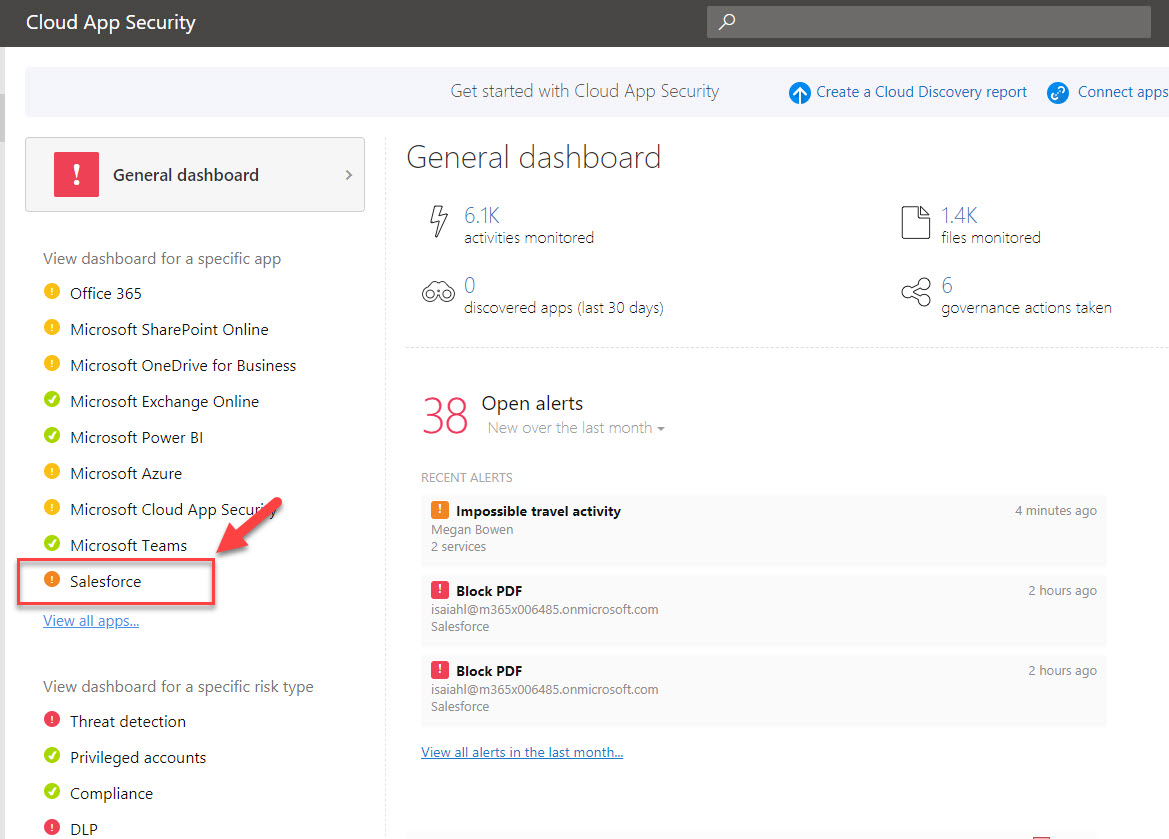
Cloud App Security Alerts. To start, we first need to open to the defender for cloud apps portal. Alerts can be filtered by alert type or by severity. Which means reporting latency for these alerts are between 2 to 4 hours. Something along the lines of the cloud discovery reporting but more detailed/customized.
 Anonymize user data in Cloud App Security Microsoft Docs From docs.microsoft.com
Anonymize user data in Cloud App Security Microsoft Docs From docs.microsoft.com
Ie microsoft add add a new policy in and then there is no alert until i manually go in and configure. In the microsoft defender for cloud apps portal, click on alerts. The flow is as follows: Alerts can be filtered by alert type or by severity. To resolve or dismiss a cloud app security alert, manage the alert in the cloud app security portal.” it doesn’t seem like the sync works either way. As new activities and events are supported by connected apps, they become available to fortisiem via microsoft cloud app security integration.
This will enable you to gain visibility into your cloud apps, get sophisticated analytics to identify and combat cyberthreats, and control how your data travels, more details on enabling and configuring the out of the box mcas connector (connect data from.
In this first article i will start to cover the basics for activity and anomaly alerts. As we already know, in todays microsoft cloud app security, we can encounter different alerts every day. It helps administrators to react faster and protect infrastructure from potential breach. This will be a series of articles on how to investigate mcas alerts. But now, this post is about o365 atp alerts, and especially o365 atp safe link alerts, in microsoft cloud app security and threat protection suite. The linear workflow is easy to follow and shows how to initially set up you connectors.
 Source: practical365.com
Source: practical365.com
Assess the risk of the service based on the app catalog. Enter a comment to explain why you dismissed the alert; Microsoft cloud app security’s activity policies allow you to enforce a wide range of automated processes using the app provider’s apis. To start, we first need to open to the defender for cloud apps portal. It helps administrators to react faster and protect infrastructure from potential breach.
 Source:
Source:
This is done by making the logs cim compliant, adding tagging for enterprise security data models, and other knowledge objects to make searching and visualizing this data easy. To do this from the alerts page in cloud app security, you can view alerts with an open resolution status. Now add an api token, and give it a name. Microsoft cloud app security alerts. This part of the cloud app security dashboard allows you to see suspicious activity or violations of any policies you’ve established.
 Source: up2.primecc.org
Source: up2.primecc.org
As new activities and events are supported by connected apps, they become available to fortisiem via microsoft cloud app security integration. As of right now we can only extract data by using advanced filters and exporting the data via excel. Dismiss an alert after you look at it and determine it�s not interesting. The image on your screen shows an example. To clarify, integration with aip will leverage sensitivity labels if you have migrated your aip labels to.
 Source: docs.microsoft.com
Source: docs.microsoft.com
This is done by making the logs cim compliant, adding tagging for enterprise security data models, and other knowledge objects to make searching and visualizing this data easy. Alerts can be filtered by alert type or by severity. To start, we first need to open to the defender for cloud apps portal. Microsoft 365 gains double key encryption security tool security tools microsoft encryption. It helps administrators to react faster and protect infrastructure from potential breach.
 Source: qwe2.ist-mind.org
Source: qwe2.ist-mind.org
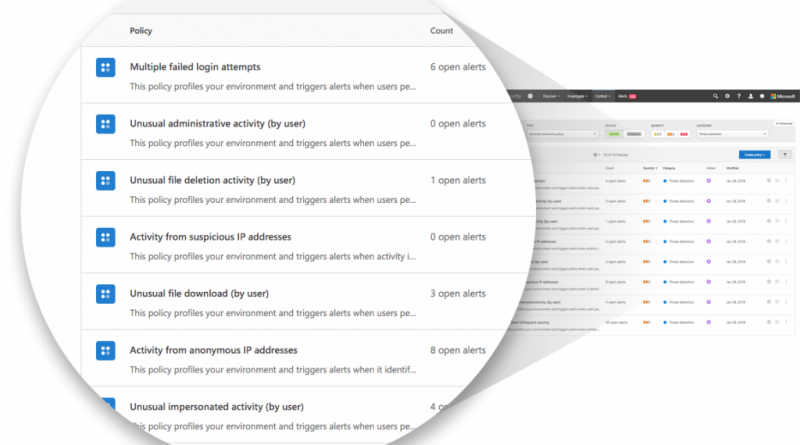
These policies enable you to monitor specific activities carried out by various users, or follow unexpectedly high rates of one certain type of activity. It helps administrators to react faster and protect infrastructure from potential breach. As new activities and events are supported by connected apps, they become available to fortisiem via microsoft cloud app security integration. Use the integration to view and resolve alerts, view activities, view files, and view user accounts. To resolve or dismiss a cloud app security alert, manage the alert in the cloud app security portal.” it doesn’t seem like the sync works either way.
 Source: docs.microsoft.com
Source: docs.microsoft.com
Fortisiem integrates with microsoft cloud app security to collect alerts and activities from apps to microsoft cloud. As of right now we can only extract data by using advanced filters and exporting the data via excel. The playbooks folder contains security playbooks templates that can be used using microsoft cloud app security connector. Send us feedback about this alert to be reviewed by our security research team for improving the alerts. At the top right, click on settings and choose security extensions.
 Source: blog.mashfords.com
Source: blog.mashfords.com
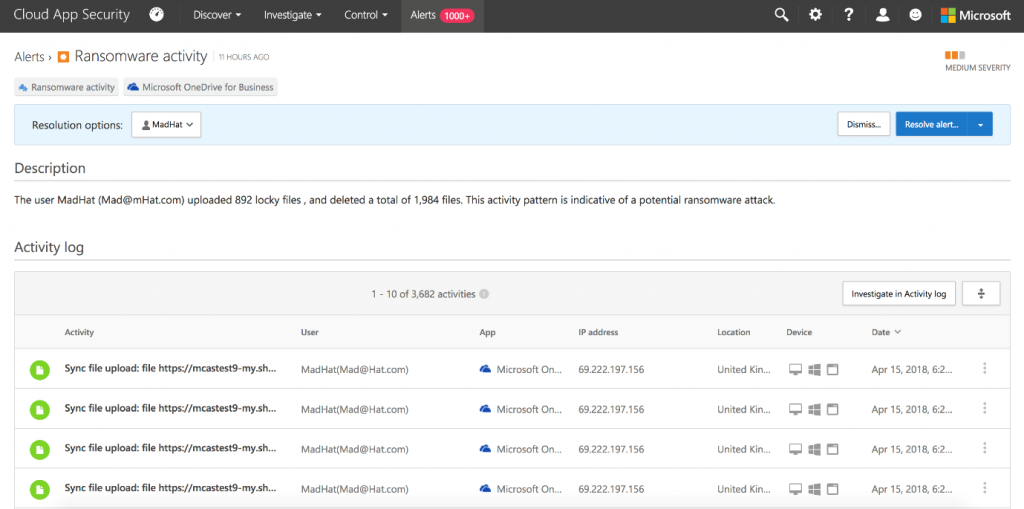
Automatic ticket generation from cloud app security alerts. Microsoft disaster recovery of azure disk encryption v2 enabled virtual machines azur disaster recovery free online learning resources free online learning. This detection policy considers past activity locations and triggers an alert when an activity occurs from a new location by any user in the company. It provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyber threats across all your cloud services. Cloud app security alerts you when suspicious actions are discovered, such as activity from anonymous it addresses, suspicious inbox forwarding configurations, ransomware activity and more.
 Source: docs.microsoft.com
Source: docs.microsoft.com
6 minutes this post walks thru an example of how to automatically apply a sensitivity label to files in sharepoint online and onedrive under certain conditions using an integration between microsoft cloud app security (mcas) and azure information protection (aip). These policies enable you to monitor specific activities carried out by various users, or follow unexpectedly high rates of one certain type of activity. This is done by making the logs cim compliant, adding tagging for enterprise security data models, and other knowledge objects to make searching and visualizing this data easy. The first demonstration david gives is how to automatically generate tickets in servicenow when there is a new alert in cloud app security. The type of data we would like to extract will be.
 Source: docs.microsoft.com
Source: docs.microsoft.com
At the top right, click on settings and choose security extensions. The integration is done via the microsoft cloud app security siem agent. The flow is as follows: The playbooks folder contains security playbooks templates that can be used using microsoft cloud app security connector. Fortisiem integrates with microsoft cloud app security to collect alerts and activities from apps to microsoft cloud.
 Source: docs.microsoft.com
Source: docs.microsoft.com
This will enable you to gain visibility into your cloud apps, get sophisticated analytics to identify and combat cyberthreats, and control how your data travels, more details on enabling and configuring the out of the box mcas connector (connect data from. Send us feedback about this alert to be reviewed by our security research team for improving the alerts. Something along the lines of the cloud discovery reporting but more detailed/customized. The first demonstration david gives is how to automatically generate tickets in servicenow when there is a new alert in cloud app security. Copy your individual token and the connection url, that is displayed.
 Source: docs.microsoft.com
Source: docs.microsoft.com
This is done by making the logs cim compliant, adding tagging for enterprise security data models, and other knowledge objects to make searching and visualizing this data easy. Copy your individual token and the connection url, that is displayed. These policies enable you to monitor specific activities carried out by various users, or follow unexpectedly high rates of one certain type of activity. To clarify, integration with aip will leverage sensitivity labels if you have migrated your aip labels to. But now, this post is about o365 atp alerts, and especially o365 atp safe link alerts, in microsoft cloud app security and threat protection suite.
 Source: blog.mashfords.com
Source: blog.mashfords.com
The type of data we would like to extract will be. In this first article i will start to cover the basics for activity and anomaly alerts. 6 minutes this post walks thru an example of how to automatically apply a sensitivity label to files in sharepoint online and onedrive under certain conditions using an integration between microsoft cloud app security (mcas) and azure information protection (aip). The integration is done via the microsoft cloud app security siem agent. We would like to show you a description here but the site won’t allow us.
 Source: docs.microsoft.com
Source: docs.microsoft.com
This alert is an alert about shadow it. To do this from the alerts page in cloud app security, you can view alerts with an open resolution status. Investigate the specific user�s activity. Assess the risk of the service based on the app catalog. The image on your screen shows an example.
 Source:
Source:
6 minutes this post walks thru an example of how to automatically apply a sensitivity label to files in sharepoint online and onedrive under certain conditions using an integration between microsoft cloud app security (mcas) and azure information protection (aip). The integration is done via the microsoft cloud app security siem agent. In the microsoft defender for cloud apps portal, click on alerts. When a high severity alert is generated by microsoft cloud app security, post a message to a slack channel or create an issue in jira. The linear workflow is easy to follow and shows how to initially set up you connectors.
 Source: docs.microsoft.com
Source: docs.microsoft.com
6 minutes this post walks thru an example of how to automatically apply a sensitivity label to files in sharepoint online and onedrive under certain conditions using an integration between microsoft cloud app security (mcas) and azure information protection (aip). Use the integration to view and resolve alerts, view activities, view files, and view user accounts. The flow is as follows: The type of data we would like to extract will be. Microsoft cloud app security is a multimode cloud access security broker (casb).

As we already know, in todays microsoft cloud app security, we can encounter different alerts every day. Something along the lines of the cloud discovery reporting but more detailed/customized. Office 365 cloud app security default alerts i must be missing something obvious here but can�t see a way to automatically add send alert as email to new detection policies. Which means reporting latency for these alerts are between 2 to 4 hours. Alerts can be filtered by alert type or by severity.
 Source: docs.microsoft.com
Source: docs.microsoft.com
As we already know, in todays microsoft cloud app security, we can encounter different alerts every day. As of right now we can only extract data by using advanced filters and exporting the data via excel. After the recent microsoft cloud app security release, the activity filtering doesn’t work as expected at the time of writing blog in may 2020. Copy your individual token and the connection url, that is displayed. But now, this post is about o365 atp alerts, and especially o365 atp safe link alerts, in microsoft cloud app security and threat protection suite.
 Source:
Source:
These policies enable you to monitor specific activities carried out by various users, or follow unexpectedly high rates of one certain type of activity. The flow is as follows: The type of data we would like to extract will be. Fortisiem integrates with microsoft cloud app security to collect alerts and activities from apps to microsoft cloud. It helps administrators to react faster and protect infrastructure from potential breach.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title cloud app security alerts by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






